which of the following are breach prevention best practices jko
A strong password will be at least 12 characters long including at least one upper case letter number. Which of the following are breach prevention best practices.
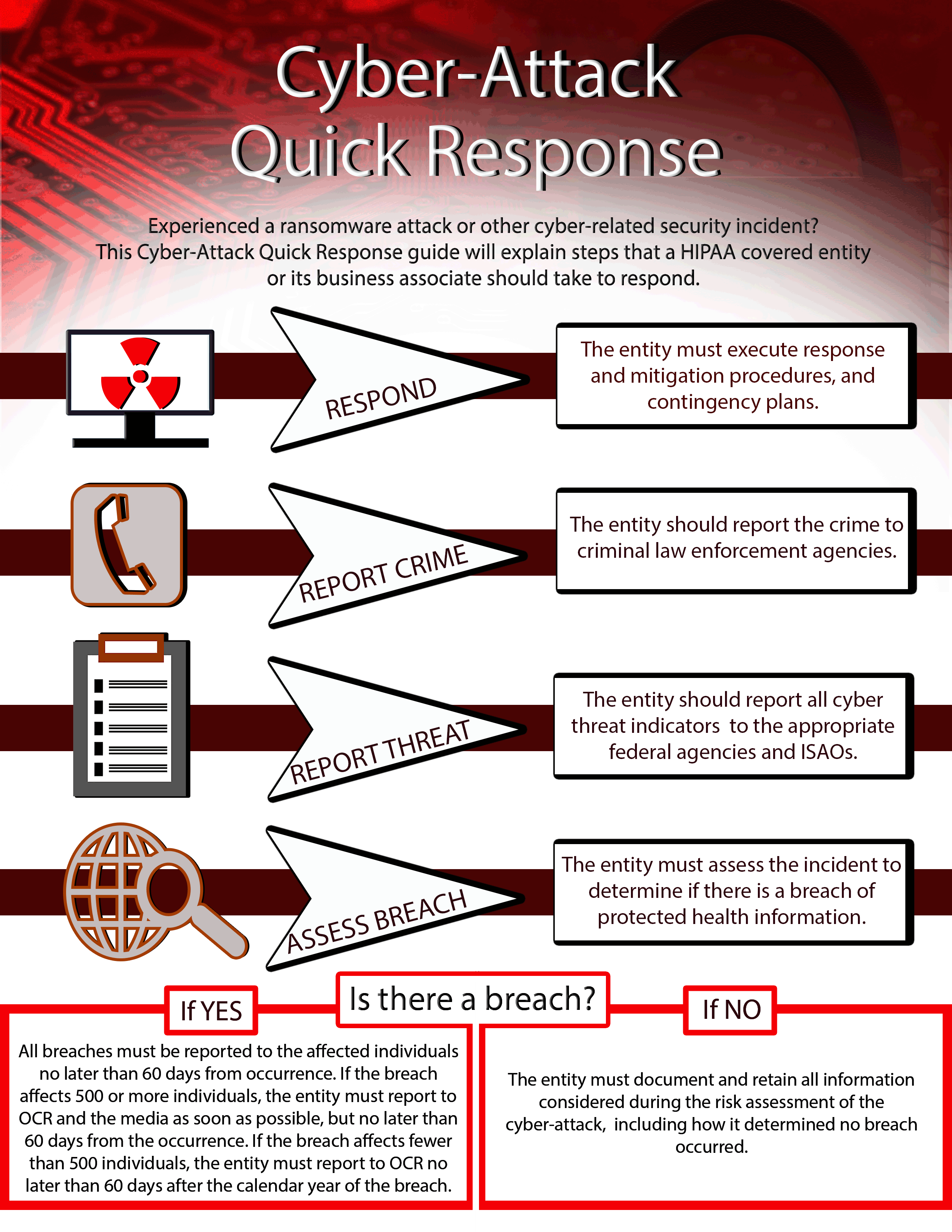
Cyber Security Guidance Material Hhs Gov
Data encryption solutions to render data inaccessible and unusable in.
. A breach as defined by the DoD is broader than a HIPAA breach or. Get insights to prevent new threats. Which of the following statements about.
Best Practices for Preventing a Data BreachTrain Employees on Security Awareness. Invest in the Right Security. Get actionable insights to stop a rise in cybercrime.
Train Employees on Security Awareness Which of the. Create Strong Policies Strong Passwords. Using strong passwords is an essential part of preventing breaches.
Data loss protection DLP to detect and prevent data breaches by blocking the extraction of sensitive information. At all levels should implement privacy and. Employees have an important role in keeping their organizations secure.
D All Of The Above. Making weak passwords can be a reason for Data. All of the above.
Select the best answer. Lets examine the best practices companies employ to protect themselves adequately from a data breach. Developing the IRP will help the IT staff of the company to control the data breach incidents.
All of the above An incidental use or disclosure is not a violation of the HIPAA Privacy Rule if the covered entity. Which of the following are breach prevention best practices. Which of the following are breach prevention best practices.
Stop advanced email security threats. Which of the following are breach prevention best practices. Ad Businesses are seeing a massive rise in cyberattacks.
4 HIPAA allows the use and disclosure of PHI for treatment payment and health care operations TPO without the patients consent or authorization.

Which Of The Following Are Breach Prevention Best Practices Public Health

Near Field Communication Nfc Technology Vulnerabilities And Principal Attack Schema Infosec Resources

Mitigating Domestic Terrorism And Insider Threat Risks Security Magazine

Hipaa And Privacy Act Training Pre Test Answers Pdf 1 In Which Of The Following Circumstances Must An Individual Be Given The Opportunity To Agree Course Hero

Oracle Corp Definitive Proxy Statement Def 14a
Hipaa Jko Training Flashcards Quizlet
Hipaa And Privacy Act Training 1 5 Hrs Jko Flashcards Quizlet

Answered Hipaa And Privacy Act Training Challenge Exam Dha Us001 Exams Nursing Docsity

A Covered Entity Ce Must Have An Established Complaint Process False True Course Hero

Scientific Program Of 34th World Congress Of Endourology Swl Program Book And Abstracts Journal Of Endourology

Biorestorative Therapies Inc Ipo Investment Prospectus S 1

Hipaa And Privacy Act Challenge Exam Docx Hipaa And Privacy Act Training Challenge Exam Joint Knowledge Online Jko Dha Us001 Select Your Current Course Hero

Top Cyber Security Informer Cso Cybersecurity Content For May 2022

Dod Cyber Awareness Challenge 2020 Your Ultimate Guide Infosec Insights

Healthcare Law Update July August 2022 Brach Eichler
Hipaa Jko Challenge Test Flashcards Quizlet

6 Which Of The Following Statements About The Privacy Act Are True All Of The Course Hero